How to Fix “Your Connection Is Not Private” Error: Complete Troubleshooting Guide
Encountering the “Your Connection Is Not Private” error can be frustrating, especially when you’re trying to access a trusted website.
This common security warning appears in browsers like Chrome, Firefox, or Safari and usually signals issues with SSL certificates, network settings, or device configurations.
In this complete troubleshooting guide, we’ll explain what causes the error, how to fix it step by step, and how to prevent it in the future, ensuring your browsing experience stays secure and uninterrupted.
What Is the “Your Connection Is Not Private” Error?
When browsing the web, you may occasionally encounter a warning message stating “Your connection is not private.” This error appears when your browser cannot establish a secure connection with the website you’re trying to visit.
This security warning is your browser’s way of protecting you from potential threats. It indicates there’s an issue with the SSL certificate of the website, which is essential for creating an encrypted connection between your browser and the web server.
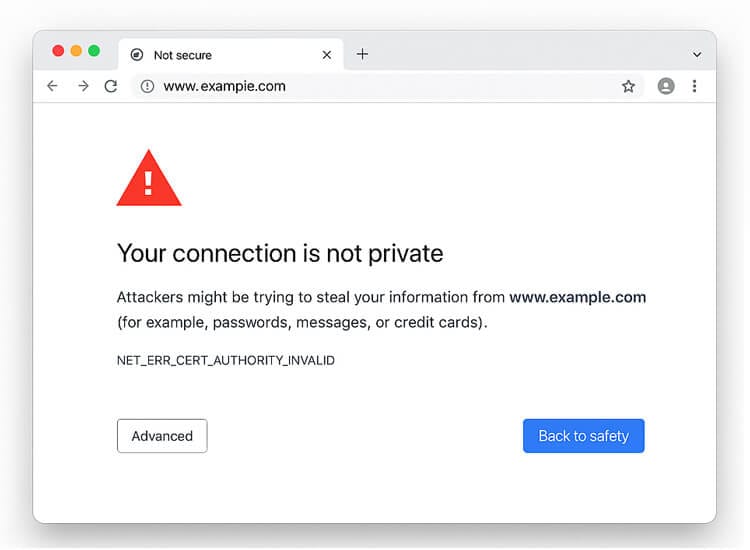
The error message varies slightly depending on your browser:
- Google Chrome: “Your connection is not private”.
- Mozilla Firefox: “Connection not secure Firefox”.
- Microsoft Edge: “Your connection isn’t private Edge”.
- Safari: “This connection is not private”.
These warnings appear alongside error codes like NET::ERR_CERT_AUTHORITY_INVALID or NET::ERR_CERT_DATE_INVALID, which provide clues about the specific issue.
Why Do You See the “Your Connection Is Not Private” Error?
Understanding why this error occurs is the first step in fixing it. Here are the most common causes:
1. SSL Certificate Issues
- Expired SSL certificate: The website’s SSL certificate has reached its expiration date
- Self-signed certificate error: The website uses a certificate that hasn’t been verified by a trusted authority
- Certificate name mismatch error: The certificate was issued for a different domain than the one you’re visiting
- Certificate authority validation problems: The certificate wasn’t issued by a trusted certificate authority
2. Browser or System Issues
Browser and system-level issues are among the most common causes of the “Your connection is not private” error, yet they’re often overlooked. Let’s examine these in detail:
Incorrect Date and Time Settings
Your browser uses your system’s date and time to verify SSL certificates. If your clock is significantly off:
- Certificates may appear expired when they’re actually valid
- Your browser may reject certificates that haven’t technically become valid yet
- The NET::ERR_CERT_DATE_INVALID error commonly appears in this scenario
This is particularly common on:
- New computers that haven’t synced time yet
- Devices with depleted CMOS batteries
- Systems that have been offline for extended periods
Outdated Browser Cache and Cookies
Browsers store information about websites, including SSL certificate details:
- Outdated cache may contain old certificate information
- Corrupted cache files can interfere with the SSL handshake process
- Browser cookies with incorrect security flags can trigger warnings
This often happens after:
- Major browser updates
- Certificate renewals on frequently visited sites
- System hibernation or sleep-wake cycles
Browser Settings and Configuration Issues
Your browser’s security settings can directly impact certificate validation:
- High-security settings may reject certificates that don’t meet certain standards
- Disabled TLS versions in advanced settings can prevent connections
- Manually installed root certificates might conflict with website certificates
- Failed previous updates may leave certificate stores in an inconsistent state
Security Software Interference
Antivirus programs, firewalls, and security suites often intercept secure connections:
- Many antivirus programs perform “SSL scanning” by injecting their own certificates
- Corporate firewalls may perform man-in-the-middle inspection of encrypted traffic
- VPN software can interfere with certificate validation, especially when using split tunneling
- Browser security extensions may enforce stricter certificate requirements than the browser itself
This is especially common with:
- Kaspersky, Avast, and Norton security suites
- Corporate VPNs and monitoring software
- Ad-blockers and privacy extensions that enforce HTTPS
DNS Configuration Problems
DNS (Domain Name System) issues can cause certificate mismatches:
- DNS poisoning may direct you to the wrong server with an invalid certificate
- Local DNS cache may contain outdated information
- Custom DNS servers might fail to resolve the correct address
- ISP DNS hijacking for advertising or monitoring purposes can break secure connections
Operating System Certificate Store Issues
Your operating system maintains a store of trusted certificate authorities:
- Outdated root certificates can cause newer website certificates to be untrusted
- Corrupted certificate stores may fail to recognize valid certificates
- Missing intermediate certificates can break the chain of trust
- System policy restrictions (common in corporate environments) may block certain certificate types
Hardware and Network Issues
Some hardware and network configurations can interfere with SSL connections:
- Misconfigured proxy servers that don’t properly handle HTTPS traffic
- Network devices performing deep packet inspection
- Captive portals in public Wi-Fi networks
- Internet Service Provider traffic shaping or filtering
- Mobile carrier data compression systems that alter secure connections
3. Network Problems
Network-related issues are frequently behind SSL certificate validation failures. These problems can occur anywhere between your device and the web server, making them sometimes challenging to diagnose. Let’s examine these network issues in detail:
Public Wi-Fi Limitations and Captive Portals
Public Wi-Fi networks often present unique challenges for secure connections:
- Captive portals: Many public networks (in cafes, airports, hotels) use captive portals that require login before allowing internet access
- These portals intercept HTTPS requests, triggering security warnings
- Your browser detects this interception as a potential security threat
- You may need to visit an HTTP site first to trigger the login page
- Traffic inspection: Some public networks perform deep packet inspection or SSL interception
- This breaks the end-to-end encryption expected by your browser
- Corporate guest networks commonly implement this for security monitoring
- Educational institutions often deploy similar technology for content filtering
- Bandwidth throttling: Some networks restrict HTTPS traffic or limit the time allowed for SSL handshakes
- This can cause timeout errors during the certificate validation process
- Mobile hotspots with poor signal strength commonly exhibit this issue
HTTPS Mixed Content Issues
Mixed content occurs when a secure HTTPS page loads resources from insecure HTTP sources:
1. Active mixed content: Scripts, iframes, or other interactive elements loaded over HTTP
- Browsers block this content by default, often breaking website functionality
- These elements can compromise the entire page’s security
- The error is more severe because active content poses higher security risks
2. Passive mixed content: Images, videos, or audio loaded over HTTP
- Browsers display warnings but may still load this content
- While less dangerous than active content, it still represents a security vulnerability
- Can trigger browser warnings about “partially encrypted” pages
3. Relative URLs: Internal links that don’t specify the protocol
- May default to HTTP instead of HTTPS when the site was recently migrated
- Particularly common in content management systems like WordPress
- Often found in older themes or plugins not designed for HTTPS
Proxy and Firewall Interference
Network intermediaries can disrupt the SSL certificate validation process:
1. Transparent proxies: ISPs or organizations may deploy proxies that users are unaware of
- These can modify HTTPS traffic in ways that trigger browser warnings
- Common in corporate environments, educational institutions, and some countries
- May be implemented for content filtering, caching, or monitoring purposes
2. SSL inspection: Enterprise firewalls often decrypt and re-encrypt HTTPS traffic
- This allows scanning for malware or policy violations
- Requires installing custom certificates on user devices
- Without proper certificate installation, it generates “connection not private” errors
3. Protocol downgrade attacks: Some network devices may attempt to force connections to use weaker security
- Modern browsers detect these attempts and refuse connections
- Can be malicious (attackers) or unintentional (misconfigured equipment)
ISP and Routing Issues
Problems with your Internet Service Provider or the route to the website can cause SSL errors:
1. DNS hijacking: Some ISPs redirect DNS requests for commercial or technical purposes
- Can cause mismatches between the requested domain and the certificate domain
- Common in hotel networks, public Wi-Fi, and some residential ISPs
- Sometimes implemented for parental controls or content filtering
2. Traffic shaping: ISPs may prioritize or throttle certain types of traffic
- Can interrupt the SSL handshake process if not properly implemented
- More common on congested networks or mobile data connections
- May target specific protocols or services
3. BGP route hijacking: Occasionally, internet routing problems occur at a global scale
- Can direct traffic to incorrect servers with invalid certificates
- Usually temporary, but can affect large regions
- Most common during major network changes or failures
Content Delivery Network (CDN) Configuration
Many websites use CDNs to improve performance, but this adds complexity to SSL implementation:
1. Certificate mismatch: The CDN edge server’s certificate may not match the original site
- Requires special configuration (like SNI support) to work correctly.
- More common with older browsers or operating systems.
- It can happen during CDN provider transitions.
2. CDN propagation delays: Changes to SSL certificates may take time to reach all CDN nodes
- During this period, some users may receive outdated certificates.
- It can happen after certificate renewal or CDN configuration changes.
- Usually resolves within hours as changes propagate.
3. IP address changes: Website IP addresses may change during CDN migrations
- Local DNS caches may retain outdated IP information.
- Can temporarily point to servers without valid certificates.
- Often occurs during website hosting transitions.
How to Fix “Your Connection Is Not Private” Error (For Website Visitors)
When you encounter this error as a website visitor, the good news is that many solutions are available without requiring technical expertise. Let’s explore comprehensive troubleshooting steps from the simplest to the more advanced options:
Quick Fixes for Browser Security Warnings
1. Reload the Page
The simplest solution is often the most effective:
- Simple refresh: Click the reload button or press F5
- Hard refresh: Press Ctrl+F5 (Windows/Linux) or Cmd+Shift+R (Mac) to bypass cache
- Wait and retry: Some certificate issues are temporary during updates or maintenance
- Try opening the link again: Sometimes, clicking the link from search results or emails works better than reloading
If the error persists after reloading, move on to more specific solutions.
2. Check Your System Date and Time
Incorrect system time is a surprisingly common cause of SSL certificate validation failures:
For Windows:
- Right-click on the time in the taskbar
- Select “Adjust date/time.”
- Toggle “Set time automatically” to ON
- Click “Sync now” to force immediate synchronization
- Ensure your time zone is set correctly
- Restart your browser and try again
For Mac:
- Click Apple menu → System Preferences/Settings
- Select “Date & Time”
- Check “Set date and time automatically”
- Select the appropriate time server from the dropdown
- Verify your time zone is correct
- Restart your browser and try again
For Android:
- Open Settings → System → Date & time
- Enable “Use network-provided time.”
- Enable “Use network-provided time zone.”
- Force close your browser from the recent apps.
- Reopen and try the website again.
For iOS:
- Go to Settings → General → Date & Time
- Enable “Set Automatically”
- Verify your time zone is correct
- Close the browser from the app switcher
- Reopen and try the website again
For Linux:
- Open terminal and enter: sudo timedatectl set-ntp true
- Check synchronization with: timedatectl status
- Restart your browser and try again
3. Try Incognito Mode to Isolate Browser Extension Issues
Browser extensions or cached data may interfere with secure connections:
How to open incognito mode:
- Chrome: Press Ctrl+Shift+N (Windows/Linux) or Command+Shift+N (Mac)
- Firefox: Press Ctrl+Shift+P (Windows/Linux) or Command+Shift+P (Mac)
- Edge: Press Ctrl+Shift+N (Windows/Linux) or Command+Shift+N (Mac)
- Safari: Press Command+Shift+N (Mac)
What to check in incognito mode:
- If the site loads normally, the issue is likely with:
- An installed browser extension
- Cached website data
- Stored cookies affecting authentication
- Custom browser settings
Finding problematic extensions:
- If incognito mode works, return to normal browsing
- Disable extensions one by one:
- Chrome: Menu → More tools → Extensions
- Firefox: Menu → Add-ons and themes
- Edge: Menu → Extensions
- Try the site after each extension is disabled to identify the culprit
- Consider removing security or ad-blocking extensions that might interfere with SSL
4. Clear Browser Cache and Cookies Completely
Clearing stored browsing data removes potentially corrupted certificate information:
For Google Chrome:
- Click the three dots in the top-right corner
- Select “Settings” → “Privacy and security”
- Choose “Delete browsing data”
- Select “Advanced” tab
- Choose time range: “All time”
- Check:
- Browsing history
- Cookies and site data
- Cached images and files
- Hosted app data
- Site settings
- Click “Clear data”
- Restart Chrome and try again
For Mozilla Firefox:
- Click the menu button (three lines)
- Select “Settings” → “Privacy & Security”
- In the “Cookies and Site Data” section, click “Clear Data”
- Check both “Cookies and Site Data” and “Cached Web Content”
- Click “Clear”
- Additionally, click “Manage Data” to remove specific site data
- Restart Firefox and try again
For Microsoft Edge:
- Click the three dots in the top-right
- Select “Settings” → “Privacy, search, and services”
- Under “Clear browsing data,” click “Choose what to clear”
- Select time range: “All time”
- Check all options, especially:
- Cookies and site data
- Cached images and files
- Permissions
- Click “Clear now”
- Restart Edge and try again
For Safari:
- Click Safari in the menu bar → Preferences
- Go to the “Privacy” tab
- Click “Manage Website Data”
- Click “Remove All”
- Go to Safari → Empty Cache
- Restart Safari and try again
5. Clear SSL State to Reset Certificate Information
Resetting the SSL state can fix certificate validation issues by clearing stored SSL information:
For Windows:
- Open Control Panel (search for it in the Start menu)
- Go to “Internet Options” (or search for it directly)
- Select the “Content” tab
- In the “Certificates” section, click “Clear SSL state”
- Click “OK” to confirm
- Restart your browser and try again
For Mac:
- Open Keychain Access (from Applications → Utilities)
- In the search field, type the domain name having issues
- Right-click on any certificates for that domain
- Select “Delete” to remove them
- Restart your browser and try again
For Chrome specifically:
- Enter chrome://net-internals/#sockets in the address bar
- Click “Flush socket pools.”
- Then navigate to chrome://net-internals/#hsts
- Enter the domain in “Delete domain security policies.”
- Click “Delete” and restart Chrome.
6. Try a Different Browser to Isolate Browser-Specific Issues
If the error persists in one browser, try accessing the website in a different browser:
- If it works in another browser, the issue is browser-specific
- Try using these browsers as alternatives:
- Chrome, if you’re using Firefox/Edge/Safari
- Firefox, if you’re using Chrome/Edge/Safari
- Edge, if you’re using Chrome/Firefox/Safari
- Safari, if you’re on Mac and using other browsers
This test helps determine whether:
- The issue is with your primary browser’s configuration
- The website has compatibility issues with specific browsers
- There’s a more fundamental problem with the website’s SSL certificate
7. Temporarily Disable Antivirus or VPN to Rule Out Interference
Security software sometimes interferes with SSL certificate validation by intercepting secure connections:
Temporarily disable antivirus SSL scanning:
- Windows Defender: Settings → Virus & threat protection → Manage settings → Disable “Real-time protection” temporarily
- Norton: Open Norton → Settings → Turn off “Smart Firewall” and “Auto-Protect” temporarily
- Avast: Right-click Avast icon → Avast shields control → Disable for 10 minutes
- Kaspersky: Right-click tray icon → Pause protection → Select duration
- McAfee: Right-click tray icon → Quick settings → Turn off “Real-Time Scanning” temporarily
Disable VPN connections:
- Disconnect from your VPN service
- Clear your browser cache after disconnecting
- Try accessing the site again
- If successful, your VPN might be interfering with SSL validation
Important security note: Remember to re-enable your security software after testing!
8. Change DNS Servers to Fix Potential DNS Issues
DNS server issues can sometimes trigger security warnings by directing you to incorrect servers:
Change DNS on Windows:
- Open Control Panel → Network and Internet → Network and Sharing Center
- Click on your connection → “Properties”
- Select “Internet Protocol Version 4 (TCP/IPv4)” → “Properties”
- Select “Use the following DNS server addresses.”
- Try these reliable public DNS servers:
- Google: 8.8.8.8 and 8.8.4.4
- Cloudflare: 1.1.1.1 and 1.0.0.1
- OpenDNS: 208.67.222.222 and 208.67.220.220
- Click OK, close all windows, and restart your browser
Change DNS on Mac:
- Open System Preferences → Network
- Select your active connection → “Advanced”
- Click the “DNS” tab
- Click “+” to add new DNS servers
- Add the same public DNS servers listed above
- Click OK, then “Apply”
- Restart your browser
Change DNS on Android:
- Go to Settings → Network & Internet → Advanced → Private DNS
- Select “Private DNS provider hostname”
- Enter dns.google or one.one.one.one
- Save changes and restart your device
Change DNS on iPhone/iPad:
- Go to Settings → Wi-Fi
- Tap the information icon (i) next to your network
- Scroll down to “Configure DNS” → Manual
- Add the DNS servers mentioned above
- Tap Save and restart your device
9. Flush DNS Cache to Remove Outdated DNS Information
Your system stores DNS information locally, which can become outdated:
Flush DNS on Windows:
- Press Windows+R to open Run
- Type cmd and press Enter
- In the command prompt, type: ipconfig /flushdns
- You should see “Successfully flushed the DNS Resolver Cache“
Flush DNS on Mac:
- Open Terminal (Applications → Utilities → Terminal)
- For macOS Monterey/Ventura, type: sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder
- Enter your administrator password when prompted
- There’s no success message, but the command works silently
Flush DNS on Chrome:
- Enter chrome://net-internals/#dns in your address bar
- Click “Clear host cache.”
- Also consider clearing HSTS data at chrome://net-internals/#hsts
10. Check for System Updates That Might Fix Certificate Issues
Outdated operating systems may have expired root certificates or security vulnerabilities:
Windows Update:
- Go to Settings → Update & Security → Windows Update
- Click “Check for updates”
- Install any available updates, especially security updates
- Restart your computer after updates are installed
Mac OS Update:
- Click Apple menu → System Preferences/Settings → Software Update
- Install any available updates
- Enable “Automatically keep my Mac up to date” for future updates
- Restart your Mac after updating
Browser Updates:
- Chrome: Menu → Help → About Google Chrome
- Firefox: Menu → Help → About Firefox
- Edge: Menu → Help and feedback → About Microsoft Edge
- Safari: Updates through Mac App Store
When You Need to Access the Site Despite Warnings
Proceed with Unsafe Connection (Use with Extreme Caution)
If you’re absolutely certain the website is trustworthy despite the warning, you can proceed:
In Chrome:
- Click “Advanced” on the warning page
- Click “Proceed to [website] (unsafe)”
In Firefox:
- Click “Advanced…” on the warning page
- Click “Accept the Risk and Continue”
In Edge:
- Click “Details” on the warning page
- Click “Go on to the webpage (not recommended)”
In Safari:
- Click “Show Details”
- Click “visit this website”
- Click “Visit Website” in the confirmation dialog
CRITICAL SECURITY WARNING:
- Only use this option when absolutely necessary and when you completely trust the website
- Never proceed on banking websites, payment pages, or when entering sensitive information
- This bypasses crucial security protections designed to protect your data
- Any information transmitted may be visible to attackers
- Consider this a temporary measure only until the site fixes its certificate issues
- Be especially cautious if you see errors like NET::ERR_CERT_AUTHORITY_INVALID, which indicate serious certificate problems
Creating Temporary Exceptions (Firefox Only)
Firefox allows creating exceptions for specific websites:
- When you encounter the error, click “Advanced.”
- Click “Accept the Risk and Continue.”
- Firefox will store this exception for future visits
- To manage exceptions: Settings → Privacy & Security → View Certificates → Servers
- You can remove exceptions later when the site fixes its certificate
Understanding When to Stop Trying
In some cases, it’s best to stop trying to access the site:
- If you see multiple different security warnings
- If the site is requesting sensitive information like passwords or payment details
- If you don’t fully trust the website or organization
- If you’re on a public or untrusted network
- If the error happens on a banking, government, or healthcare site
In these cases, consider:
- Contacting the website owner about the certificate issue
- Checking the company’s social media for announcements about website issues
- Using an alternative official channel to conduct your business
- Returning to the site later when the issue might be resolved
Support Genix
WordPress Support Ticket Plugin
Take Your Customer Support to The Next Level and Boost Customer Satisfaction Rates
How to Fix SSL Certificate Issues (For Website Owners)
If you’re a website owner experiencing the “Fix website not secure warning” problem, here’s how to resolve it:
1. Check Your SSL Certificate Status
Verify if your certificate is valid and properly installed:
- Use online tools like SSL Labs or WhyNoPadlock to check your certificate
- Confirm the expiration date hasn’t passed
- Ensure the certificate is issued for the correct domain
2. Install or Renew Your SSL Certificate
If your certificate has expired or isn’t properly installed:
- Obtain a new certificate: Purchase from a trusted provider or use free options like Let’s Encrypt
- Install SSL certificate WordPress: Follow your host’s instructions for installation
- SSL certificate installation WordPress often requires:
- Generating a Certificate Signing Request (CSR)
- Submitting it to a Certificate Authority
- Installing the certificate files on your server
Most WordPress hosting providers offer one-click SSL installation tools in their control panels.
3. Configure HTTPS Redirection WordPress
Ensure all traffic is directed to the secure version of your site:
- Edit your .htaccess file (Apache) or server blocks (Nginx)
- Add proper redirection rules
- Or use WordPress plugins like Really Simple SSL for automated HTTPS redirection WordPress setup
4. Fix Mixed Content Issues
Mixed content occurs when your HTTPS pages load resources (images, scripts, etc.) from HTTP sources:
- Use tools like Why No Padlock to identify mixed content
- Update internal links to use HTTPS instead of HTTP
- Check for hardcoded HTTP URLs in your theme files, widgets, and plugins
5. Address Certificate-Specific Errors
1. Fix ERR_CERT_AUTHORITY_INVALID
This error indicates your certificate isn’t trusted:
- Ensure you purchased your certificate from a trusted provider
- Install the complete certificate chain (including intermediate certificates)
- Avoid self-signed certificates on production websites
2. Fix NET::ERR_CERT_DATE_INVALID
This occurs when your certificate date is invalid:
- Renew expired certificates immediately
- Set up auto-renewal to prevent future expirations
- Ensure your server’s time is set correctly
3. Fix ERR_CERT_COMMON_NAME_INVALID
This error means the certificate doesn’t match the domain:
- Ensure your certificate covers both www and non-www versions of your domain
- Get a wildcard certificate if you have multiple subdomains
- Check that you’re accessing the site using the exact domain name on the certificate
WordPress SSL Issues and Customer Support Systems
If you manage a WordPress site with a customer support ticketing system, SSL issues can severely impact user experience and security:
Importance of SSL for Support Systems
- Protects sensitive customer information
- Builds trust with users submitting tickets
- Prevents security warnings that may deter customers
- Required for PCI compliance if handling payment information
WordPress SSL Issues Common in Support Systems
Customer support ticketing systems on WordPress frequently encounter unique SSL challenges that can disrupt service and erode user trust:
- Plugin Compatibility Conflicts: Many support plugins contain hardcoded HTTP URLs or use AJAX calls that trigger mixed content warnings. Legacy ticket management plugins often lack proper HTTPS support, causing forms to malfunction when submitted securely.
- File Upload Security Vulnerabilities: Support systems that accept file attachments require special consideration. Improperly configured SSL can expose uploaded customer documents or create submission errors when large files are transmitted over secure connections.
- API Integration Complications: Third-party integrations with CRM systems, email services, or knowledge bases may use outdated API endpoints. These connections often break during SSL migrations, causing ticket synchronization failures or automated response issues.
- Database URL References: WordPress stores absolute URLs in its database, making SSL migrations challenging. Support ticket history and attachment links frequently break during HTTPS transitions without proper database updates.
- Customization Code Conflicts: Custom theme modifications or ticket system adaptations often introduce HTTPS incompatibilities. These custom code elements require thorough testing to ensure they don’t trigger browser security warnings.
Customer Support Website Security Best Practices
Implementing robust security for WordPress support ticketing systems requires a multi-layered approach:
Enforce site-wide HTTPS with proper redirection rules and HSTS headers to prevent downgrade attacks. Regularly audit your SSL implementation with tools like SSL Labs, looking beyond the padlock for configuration weaknesses that might compromise customer data.
Install security plugins like Wordfence or Sucuri alongside your support system to provide real-time monitoring for suspicious activities targeting your ticketing forms. Implement strict input validation and output encoding to prevent ticket-based XSS attacks, which frequently target support systems.
Configure proper Content-Security-Policy headers to prevent unauthorized script execution within your support portal. This protects against malicious file uploads and cross-site scripting attempts through support tickets.
Enable two-factor authentication for all support staff accounts, as these privileged users have access to sensitive customer information. Implement IP-based access restrictions for administrative functions and regular security training for team members handling support requests.
Finally, establish a regular backup schedule with encrypted off-site storage to ensure business continuity should security incidents occur.
Preventing Future SSL Connection Errors
Proactive SSL certificate management is vital for uninterrupted website functionality and user trust. The following measures will help you avoid common issues like the “Your Connection Is Not Private” error.
- Implement Certificate Lifecycle Management: Automate certificate renewals using tools like Let’s Encrypt with certbot or hosting provider integrations. Use monitoring services to catch approaching expirations early. Assign renewal responsibilities and set up alerts via email, SMS, calendars, and Slack. Monitor certificate transparency logs to detect unauthorized certificates and audit your active certificates regularly.
- Deploy Comprehensive Monitoring Solutions: Use tools like SSL Labs or Uptime Robot to monitor all domains and subdomains. Check for expiration, weak cipher suites, or configuration errors. Set alert thresholds at multiple intervals (90/60/30 days) and establish escalation processes. Internally, integrate certificate checks into CI/CD pipelines and verify after system updates.
- Implement Technical Safeguards: Strengthen SSL implementation with HTTP Strict Transport Security (HSTS), OCSP stapling for better revocation checking, and certificate pinning for critical apps. Ensure proper fallback mechanisms and maintain backup certificates. Test all configurations thoroughly to prevent misconfigurations from impacting site accessibility.
- Establish Organizational Processes: Keep a centralized inventory of certificates with renewal dates, ownership, and dependencies. Enforce change management through staging, rollback planning, and scheduled updates. Conduct quarterly security audits to ensure ongoing compliance and best practice alignment.
- Educate and Train Team Members: Train DevOps and support teams on SSL/TLS protocols and response procedures. Assign certificate ownership roles, define escalation paths, and run simulated scenarios to prepare for emergencies. Include SSL awareness in security training for broader team engagement.
- Apply Technical Best Practices: Optimize your certificate strategy by using wildcard or multi-domain certificates wisely. Configure modern cipher suites that support Perfect Forward Secrecy, and disable insecure ones. Use CAA DNS records and standardize certificate authorities when possible. Keep backup certificates ready and tested for emergency deployment.
Frequently Asked Questions
Why do I see the “Your connection is not private” error only on certain websites?
The error appears on sites with SSL certificate issues. If you see it on many sites, the issue is likely with your browser or system.
Is it safe to proceed anyway when I see this warning?
Generally, no. Only proceed if you completely trust the website and aren’t entering sensitive information. For banking or shopping sites, never bypass this warning.
How often do SSL certificates expire?
Most SSL certificates are valid for 1-2 years. Let’s Encrypt certificates expire every 90 days and require regular renewal.
Will installing an SSL certificate affect my WordPress site’s performance?
Modern SSL certificates have minimal impact on performance. In fact, HTTPS is required for HTTP/2, which can improve site speed.
What’s the difference between free and paid SSL certificates?
Free certificates (like Let’s Encrypt) provide the same encryption strength as paid ones but may offer fewer features like warranty protection or extended validation.
Can I install multiple SSL certificates on one WordPress site?
A single SSL certificate can cover multiple domains and subdomains (with a wildcard certificate). You typically don’t need multiple certificates for one site.
Conclusion
Resolving the “Your connection is not private” error is essential for both website visitors and owners. For visitors, it ensures safe browsing experiences. For website owners, particularly those running customer support systems, it maintains trust and protects sensitive information.
By following the troubleshooting steps outlined in this guide, you can quickly diagnose and fix SSL certificate issues, maintain proper HTTPS implementation, and ensure your website remains secure and accessible to all users.
Remember that website security is an ongoing process. Regularly check your SSL configuration, stay alert for certificate expiration notices, and keep your systems updated to protect your site and its visitors.